Cyber Security Platform
Creating an Open Source Intelligence platform
Background
The business had been performing Cyber Security functions for a number of years. The Open Source Intelligence part of the business had automated all the functions, but most of these were separate components. This opened up the opportunity to find efficiencies in the internal workflow, but also significantly improve the client experience by means of a SaaS approach.
My role
As the only Product Manager in the business, I naturally took a central and leading role on the project. I coordinated much of the process, and liaised with many people across the business to establish the product. I researched and interviewed Jobs-to-be-done, designed the UI of the product, and then later moved on to do the Go-to-market plan, and write content collateral.
Discovery (Understanding the problem)
Cyber Security as a sector has grown rapidly over such a short period. And it continues to grow. Concepts such as Best Practice and Industry Standards have grown organically, and in some cases, still awaiting sanction from a consortium of professional businesses. The rapid speed and growth of Cyber Security means that in some cases, even those who work in the sector find it difficult to cite widely recognised authorities. This seemed to be part of a wider change, and something also observed during my research for CheckSafe and Amplify.
User interviews
I studied a number of our top clients, who explained their Information Security practices, with a focus upon defining what their practice looked like when it’s at it’s best, what they would want to achieve in a ‘perfect world’, what happens when things go wrong, and what ‘bad’ looked like (in terms of not being able to achieve their outcomes, typical barriers etc).
The research revealed a number of crucially important aspects for the prospective product:
- The importance of context – isolated events are often related in some way by wider factors which much also be revealed in order to understand relationships between events.
- Jargon is a distinct feature of Cyber Security – terms like ‘Attack pattern’, ‘Defence Posture’ etc were prolific in the interviews, but not all professionals shared the same opinion about what they meant, suggesting that many of the terms are not conventions of the field.
- Appeals to Authority – many of the professionals interviewed cited the use of MITRE’s Att&ck (sic) Framework, and open-sourced resource designed for professionals. There were also lots of references to machine-to-machine naming conventions (TAXII), CybOX, MAEC and STIX (Structured Threat Information eXpression). These resources were highly valuable to the role of a cybersecurity professional.
- Missing something is the biggest cause of anxiety – because of the very real business impact a cyber security breach could cause to a digitalised business, the search for evidence and data-points is always on the mind of the professional. Once they are gathering Big Data, then the issues transfers into one of consumption and meaning – such that the professional seeks ways to categorise the threats in order to address their resolutions.
Desk research based upon surveys from Gartner, McKinsey and Forrester also corroborated at a larger scale some of the evidence expressed by the people I had interviewed.
Ethnography
I also conducted ‘Safari’ sessions with members of the internal Cyber Security team to understand their current processes, observe the manners in which they interacted and discussed the field between them, as well as exploring why some behaviours and processes are performed in some ways and not potentially in others.
Competitor analysis
As with any growing sector, there was a massive surge in technical SaaS-based solutions to these challenges. I attended numerous expos, webinars and events to listen to talks provided by key competitors such as Digital Shadows, BitSight, LookingGlass, RiskIQ, RecordedFuture et al. I explored both their business models, as well as the structure of their interfaces to understand how they had also answered some of the challenges the User Research had identified.
User Stories & Product Roadmap
In order to begin the process for the Software Engineering team, I translated the problems into statements of their Jobs to be done. These User Stories allowed the Engineering team to begin to find solutions for them. There were three categories of User Stories:
- As an Super-administrator of the platform…
- As an Information Security Officer (client)…
- As a Cyber Security investigator (Cyber team)…
This meant the technology became a platform for the interaction between these 3 types of users.
Prototyping a solution
As part of answering some of the challenges I had heard, and consolidated into User Stories, I put together a set of wireframes, and then interactive prototypes to test some of the ideas which originated from those sessions.
The tool used to do this was Axure.
Testing was conducted internally, as well as with clients I had originally interviewed in order to explore and understand further how whether my mental-model was accurate. We went through a number of iterations to add pieces of the process which were also important, as well as reducing a number of features down in order to expedite the required outcomes on the part of the professional.

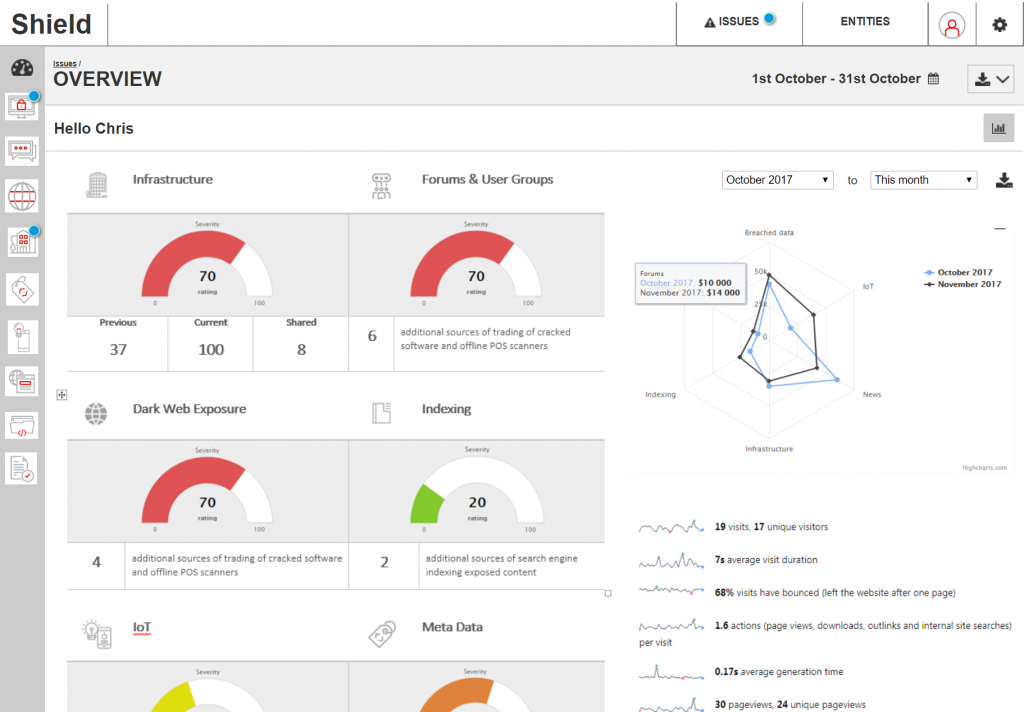
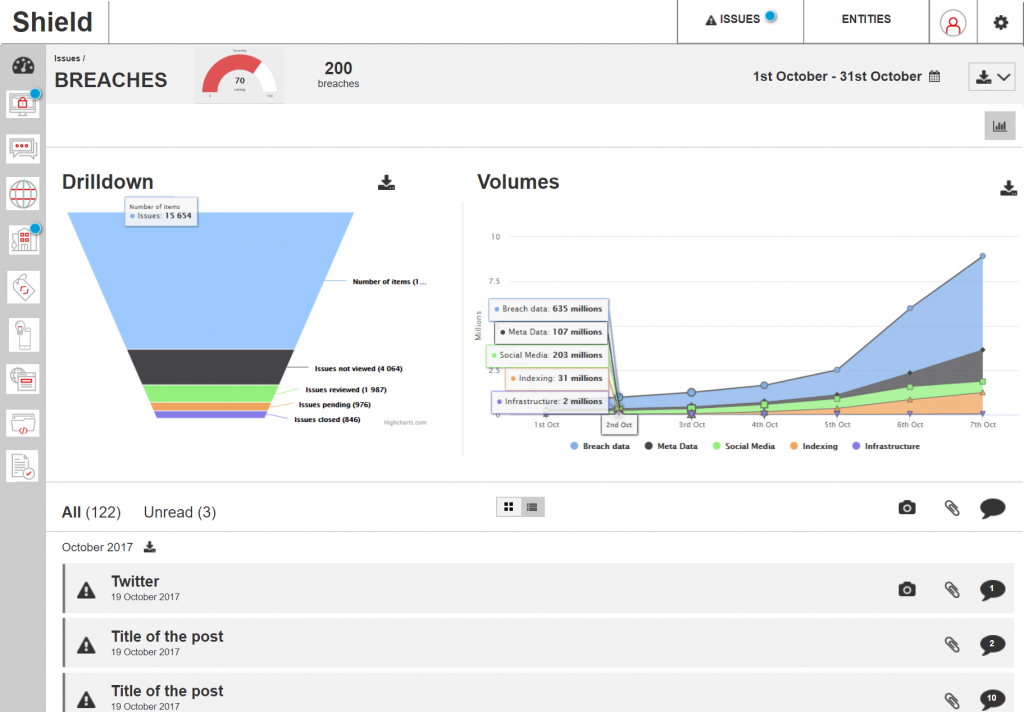
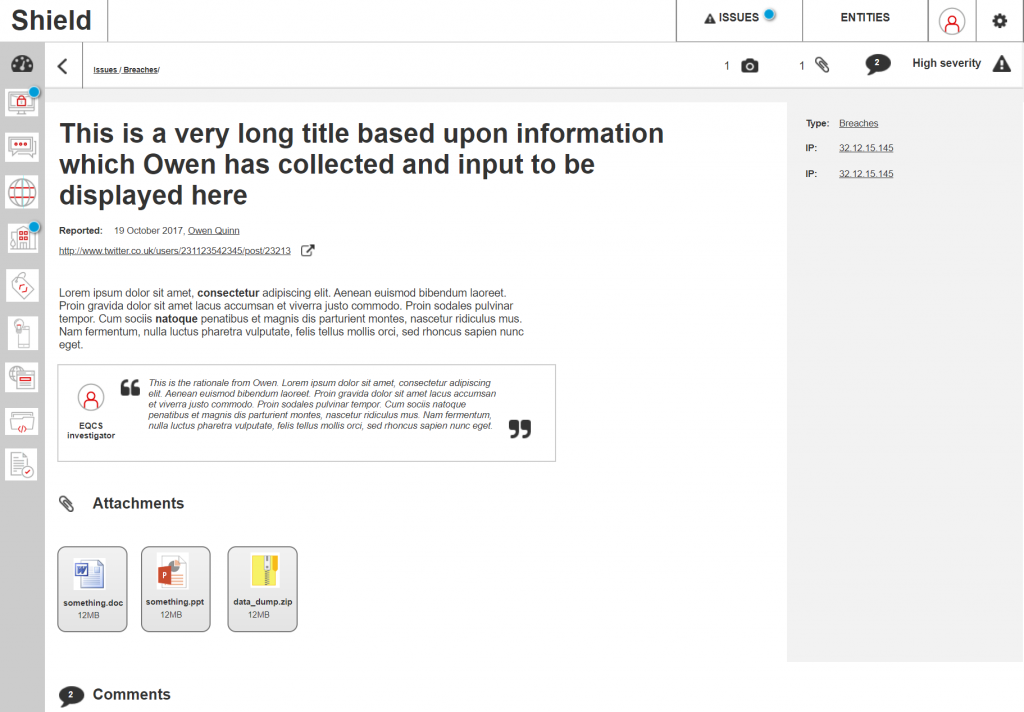


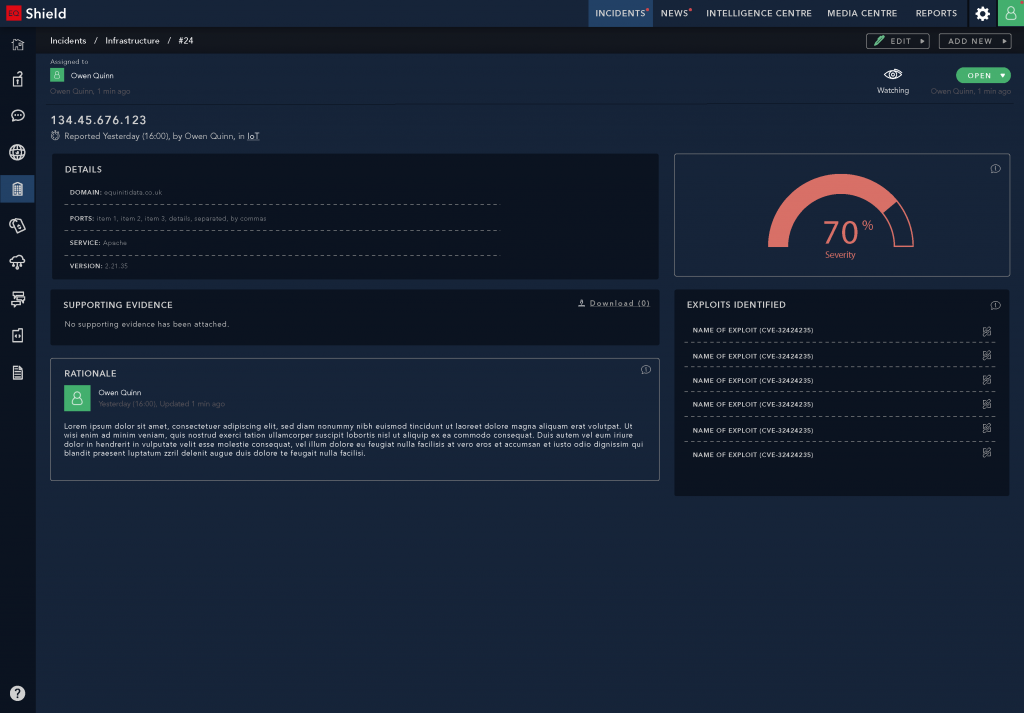
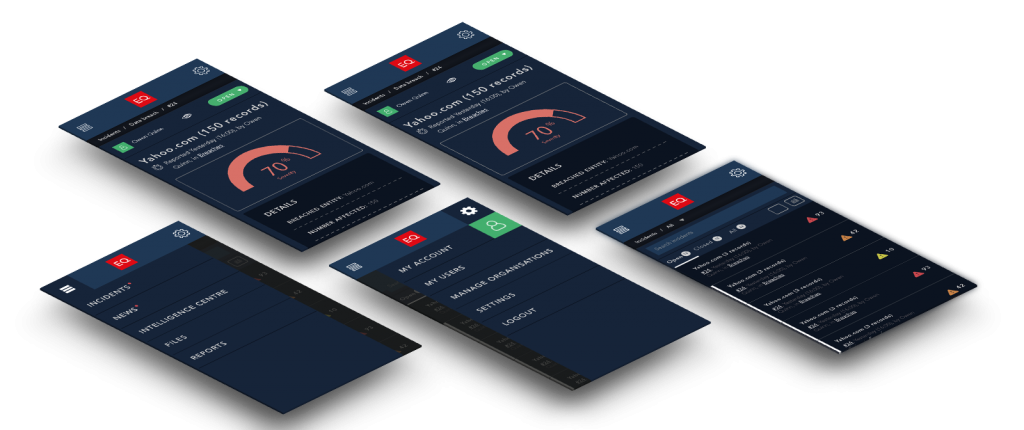
High-fidelity UI Design
I selected Adobe Illustrator and Photoshop as a means to translate the Prototype into High-fidelity.
The team and I had worked on a ‘midnight mode’ styleguide, as a means for allowing appropriation of an interface through configuring its look-and-feel. This also supported Accessibility guidelines, to ensure that users could manipulate colour schemes to suit their needs and preferences. This ‘midnight mode’ was a configurable setting in the interfaces of all the other Products which were designed at this time.
In order to draw visual distinction from the data and marketing products in the business (which used the ‘daylight mode’ as default), we made use of the ‘midnight mode’ as default. This selection was also made because it lended familiarity and parity with competitors, as well as an intuitive approach based upon the kinds of technologies our clients were using. The setting was only a default, and could be changed to suit user preference.